As a fiat-money person interested in the democratic politics of money, I’ve always viewed crypto primarily in terms of two aspects:
a. The mistrust towards states and governments often expressed by crypto’s proponents.
b. The artificial scarcity of bitcoin issuance. With its fixed and arbitrary upper limit of 21 million coins, bitcoin is far more restrictive and deflationary than the gold standard. After all, the stock of gold has proven to be something we can expand.
Source: Researchgate
Whereas the gold standard promised, roughly, that the value of money would remain stable, bitcoin, were it actually to enter widespread use as a stable currency, would be more or less guaranteed to appreciate over the longer term. And no, that is not a good thing. An appreciating currency is not better than a stable or mildly inflating currency. It is far worse. A growing economy denominated in bitcoin would deflate. That would be crippling for debtors and business. The macroeconomic costs would dwarf any conceivable efficiency gains from a decentralized crypto currency.
Researching material for the recent Ones and Tooze episode on crypto I actually went back to the founding 2008 paper by Satoshi Nakamoto on, “Bitcoin: A Peer-to-Peer Electronic Cash System”. And I dug into some of the blogposts that came out in the same period.
They contain some striking passages. Take this 2009 blogpost for instance:
“The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.”
Satoshi Nakamoto then describes how cryptographic tools could eliminate the need for trusted data administrators and declares, “It’s time we had the same thing for money. With e-currency based on cryptographic proof, without the need to trust a third party middleman, money can be secure and transactions effortless.”
Trust and the cost of generating trust are the key issues. I will return to that theme in a future post.
Here I want to focus on the cryptography itself. Yup …
For a non specialist, the Satoshi Nakamoto papers are challenging. When I say “read”, I should probably say “read in”. I’m no computer scientist so, at first, I wasn’t following the lingo or some of the concepts. But, I was determined to learn, so I turned to Eswar Prasad’s 2021 book The Future of Money.
If you need an introduction to public and private keys and cryptographic hash functions, I strongly recommend Prasad’s book. It conveys key concepts with admirable clarity.
Primed with Prasad’s explanations of the software basics, I began to realize the importance of key parts of Satoshi Nakamoto’s paper. And one bit really leapt out at me.
For a project that is commonly described as being anarcho-capitalist, the source of bitcoin’s core cryptographic software is surprising.
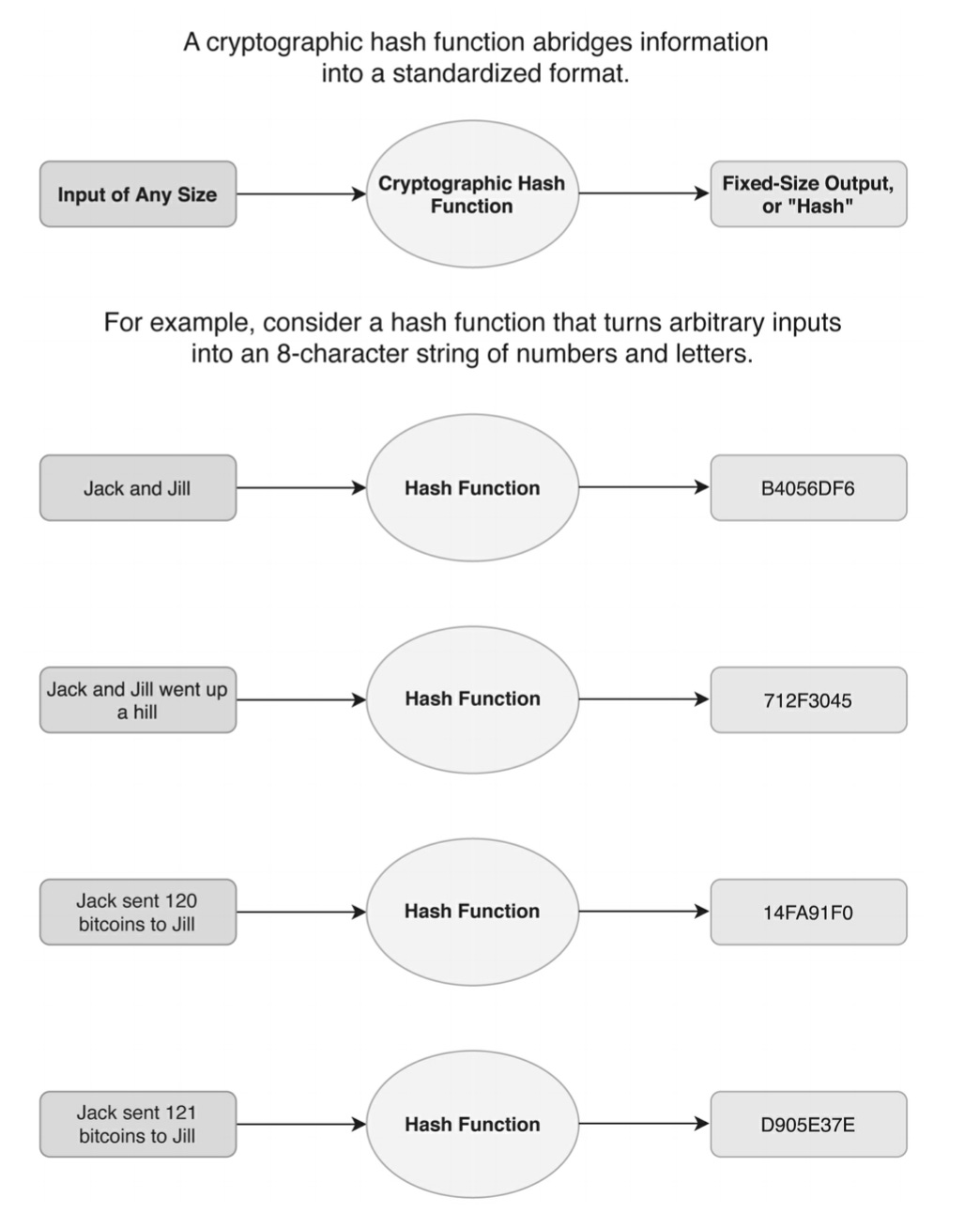
Bitcoin relies on a hash function called SHA-256. As this excellent medium post explains, SHA-256 isn’t strictly speaking a cryptographic tool because though it converts any input into a digital output of a fixed length, the process cannot be reversed by systematic means. A hash function codes, and it codes in a particularly important way. Any input generates an output of a standard format and different inputs are guaranteed to produce different output. The risk of “collisions”, when two different inputs generate the same output from the function, is very, very low. But, crucially, there is no systematic way of reversing the operation of a hash function. Once the sausage is made you can’t reverse back to the ingredients. This is a tool for encoding but not for decoding.
Source: Prasad, The Future of Money
And that, if I understand it correctly, is the point.
Because there is no way of cracking SHA-256 and reversing its transformations by systematic means, you can only reverse them by brute force, i.e. by guessing, which is the “proof of work” that bitcoin miners apply all that energy to producing.
As Prasad puts it;
The Proof of Work protocol requires miners to use their computational power to solve a randomly generated cryptographic problem that involves hashing. These problems are generated automatically by the Bitcoin algorithm, with no human intervention. The problems are mathematical puzzles whose difficulty level is measurable (a feature that will play an important role later) and that can be solved only by using brute computing power. The nature of the problems, which involves finding an input that (using the SHA-256 hash function) yields a hash that satisfies certain conditions, is such that there are no analytical tools that can possibly solve them more efficiently. In essence, a computer has to guess the solution to a problem until it finds one that works—faster computers with more computing power can speed up the guessing process, but brute force is the only way to solve the puzzles. Powerful computers can guess millions of possible solutions per second, so the problems have to be really difficult to crack. Because there is no way other than using raw computing power to crack these puzzles, solving them demonstrates proof of (computational) work.
Source: Prasad, Eswar S.. The Future of Money (p. 121). Harvard University Press. Kindle Edition.
NB readers: If I am getting this even half right, we are ahead in the game!
Anyway, my question is, what is the source of this mysterious hash function SHA-256 that defies efficient reverse engineering and forces miners to use super-fast computers to find the right answer by trying every possible combination?
SHA-256 is part of a family algorithms. And if you ask google about it, Wikipedia tells you the following:
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001.[3][4] They are built using the Merkle–Damgård construction, from a one-way compression function itself built using the Davies–Meyer structure from a specialized block cipher.
SHA-2 includes significant changes from its predecessor, SHA-1. ….
SHA-2 was first published by the National Institute of Standards and Technology (NIST) as a U.S. federal standard (FIPS). The SHA-2 family of algorithms are patented in US patent 6829355.[6] The United States has released the patent under a royalty-free license.[7]
Hang on, what?
One of the core pieces of software in bitcoin, a system of currency supposedly designed to minimize reliance on government was created by America’s digital spymasters in chief, the NSA, published by the National Institute of Standards and Technology and is made available to the public under a royalty-free patent.
My question is this: Shouldn’t the origin of SHA-256 upend a large part of the crypto narrative?
Has anyone else been struck by this? I’ve done a fair amount of googling, but the only person I can find who even raised an eye-brow is Donald MacKenzie in a piece in the LRB in 2019.
But MacKenzie raises the issue only to dismiss it. This is the critical passage:
You don’t have to be overly paranoid to pause for a few seconds when you learn that the lineage of the crucial technical component of bitcoin includes an intelligence agency renowned as the world’s premier code-breakers. As far as I can see, though, there are no real grounds for worrying that the NSA has built in a subtle flaw so that it can decrypt messages scrambled using SHA-256. The algorithm was made public by the US National Institute of Standards and Technology, and the steps in it are simple enough that a ‘back door’ of this 5 kind would be hard to conceal. By the time that SHA-256 was first released, in 2001, the NSA seems to have realised that it would be foolish to insert a back door into cryptographic techniques that were going to be used widely in the civilian world. Those techniques are utterly central to everyday electronic commerce and to the global financial system. If the bad guys were to discover the back door, chaos would ensue.
I have HUGE respect for MacKenzie, but, to my mind, this is to miss the point. The really interesting issue is not whether the NSA has built a trap door into the software, though that would be sensational, the issues are:
What does it mean that a cryptocurrency project that is supposedly intended to substitute for trust in government in the creation of money, in fact, relies in its core on government-generated software. Does it mean that the politics of crypto are self-deluding? Or are they best understood not as anti-government in general, but as hostility to particular branches of government? Satoshi Nakamoto does not trust the central bank, but Satoshi Nakamoto unhesitatingly employs material from the NSA, approved by the NIST and available under a free license. Why is this? Is there a distinction at work here between technical branches of government (NSA, NIST) and political branches (the Fed, fiat money etc)? Or is there an underlying sociology of professional expertise which means that Satoshi Nakamoto and his ilk trust their counterparts at the NSA and NIST because they are essentially part of the same expert community? On the other hand economists are predisposed to trust fiat money because “people like them” run the Fed?
Or is there a more fundamental materialist logic at work here. The fact that this ultra-strong cryptographic software should have been generated by the NSA is no-accident. It points to the unique computing resources and IT-expertise commanded by the state. So is crypto, like so much other digital innovation, in fact, the unacknowledged spin-off of publicly-funded investment? Bitcoin advocates are only too happy to unquestioningly avail themselves of the state when it is the NSA, NIST and patent office because those organizations are recognized as providing something useful, whereas the Fed is viewed as part of a parasitic and expensive bureaucracy that should be rationalized away. This would seem to fall under the logic of instrumentalization, exploitation and denial of the state that Mariana Mazzucato and her colleagues have highlighted.
I don’t really have answers to these questions. They seem important and I would love to know whether anyone else has raised and answered them already. All I can say for now is that I’ve done due diligence search-wise and have come up empty.
The same is pretty much true for the history of SHA-256. Wikipedia tells us the following: Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS). The first one SH-O seems to have appeared in 1993. SH-1 was the product of the US government’s Capstone project that seems to have attracted a lot of controversy in the cryptography community in the 1990s and early 2000s around the issue of backdoors and “trust management”.
But all of this took place both before the arrival of bitcoin and the harnessing of a vision of a new economy to cryptography tools. It also took place before 2013 and the Snowden revelations. To further complicate matters, Snowden, it seems, is a big crypto fan.


So you trust the code not its author?
Obviously, I’m not advocating for a further twist in the spiral of distrust, what I find fascinating is that a surge in distrust seems, dialectically, to affirm trust in something else.
If someone can put me straight about all this, I would really appreciate it.
*******
I love putting out Chartbook. I am particularly pleased that it goes out for free to thousands of subscribers around the world. But it is voluntary subscriptions from paying supporters that sustain the effort. If you are enjoying the newsletter and would like to join the group of supporters, press this button and pick one of the three options:
Thanks for reading! And share with your friends.




You ask "My question is this: Shouldn’t the origin of SHA-256 upend a large part of the crypto narrative?" and say "So you trust the code not its author?".
For computer science/math types, your question is a guilt by association question. So it's not that nobody has noticed, but rather to the STEM mindset that question is silly.
Here's a thought example to illustrate. Suppose in an alternate reality, Adolf Hitler discovered the pythagorean theorem. That in a right triangle, the length of the sides are related by a^2 + b^2 = c^2. Now, you say all these people who use this math identity should be questioning their work because of the origin of that particular piece of math. Since that was from a bad bad bad person. It's Hitler math. It's a guilt by association claim. Or use an even simpler example, 2+2=4 was discovered by Hitler. So anyone who adds 2+2 should question that bad bad bad source of that bit of math.
Now, to you, SHA-256 seems exotic and complicated. And hard to believe. But to people who use this math in the real world, it's merely another 2+2=4 basic piece of every day math. The inventor of it does't mean the math is bad. Math is an identity. It has no moral valence. Of course you can use math in a bad way. But to people who use it, once that math is out in the world, it's just another tool in the toolkit, and the providence of it just doesn't matter.
Maybe it matters to you, because it is appears so complex and odd. But to people who use these tools, it's just another software math library call. So your question will get completely ignored by people who actually use these tools. Why? It will appear to them as a very weird claim they shouldn't add 2+2=4 because the historic originator of that math was someone they are supposed to hate.
> Or is there an underlying sociology of professional expertise which means that Satoshi Nakamoto and his ilk trust their counterparts at the NSA and NIST because they are essentially part of the same expert community?
The cryptographic community doesn't trust standards like SHA because they were created by NIST or the NSA; they trust these standards because they have looked at it themselves and failed to break it in practice. Cryptographic algorithms like SHA are under constant scrutiny by the community of security researchers, both in academia and in industry, that look for ways to break their security.
More recent NIST standards like SHA-3 and AES (the U.S. standard for encryption) are the results of multi-round competitions with participants from all around the world. Both competitions ran for ~4 years, and candidate algorithms are examined both by NIST and by the wider community publishing papers and cryptanalysis results left and right. For the winning algorithms, the cryptographic community has had so much time to look at them that trust in either NIST or the NSA is not required, since any "funny business" would have probably revealed itself in the process.
As an aside, we do have one known instance of the NSA attempting to backdoor a cryptographic standard (Dual EC DRBG), and it went poorly: researchers almost immediately found the suspicious part of the standard, and nobody went out of their way to use it. The NSA had to bribe RSA Security to use it as a default in their software for the backdoor to actually be deployed somewhere promient and enabled by default. The NSA probably doesn't actively try to backdoor NIST standards anymore not because of some sense of alturism; it is just very difficult and probably leads to embarrassment further down the line when it gets found out.